Digital Transformation and the Future of Work: What Businesses Need to Know.Digital transformation has been a buzzword in the business world for several years now, and for good reason. With the rapid advancements in technology and the growing demands of consumers, companies must adapt to stay competitive.
A Summary of Smartsheet Future of Work Management Report 2023 The emergence of ChatGPT serves as a reminder that the world is undergoing a transformation and advancing towards the age of AI. The crucial question that remains unanswered is whether human beings will be replaced by AI in the future. To prevent this catastrophic outcome, we must strive to keep pace with the world's evolution by adopting new technological tools and integrating them into our daily lives. This not only ensures our survival in an AI-dominated world but also facilitates our productivity and adaptability in a rapidly changing environment.
Issue : Unable to access Smartsheet account on my Web Browser 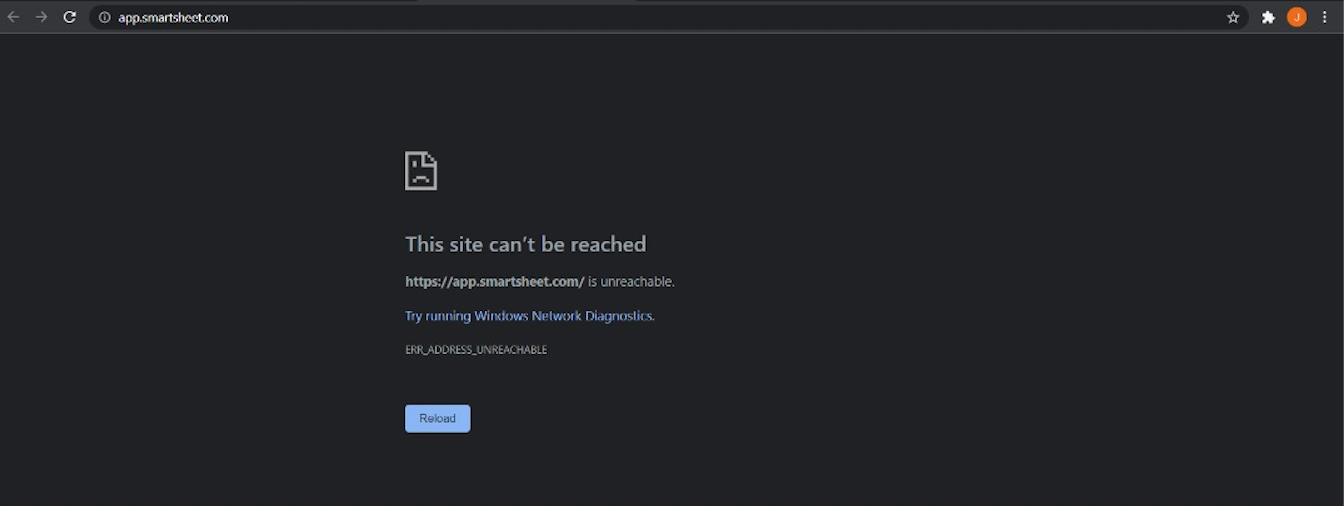 Most of the time, we seen this issue is mainly caused by the user's hardware and browser. The browser clearly indicated the error message as "This site can't be reached https://app.smartsheet.com is unreachable" The bottom of the message also provided "Try running Windows Network Diagnostics" Kindly refer to these two-steps guide mentioned below and follow the best-practice guide, and your problem will be mostly resolved forever. Step 1 : Check Hardware
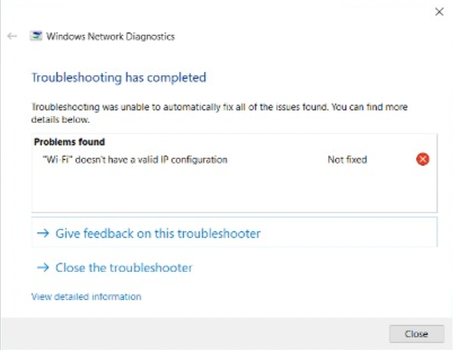 👈🏻 If your Windows's Network Card (WiFi or Ethernet Cable) doesn't have a valid IP configuration, please refer to this fix guide : https://windowsreport.com/wi-fi-valid-ip-configuration-windows-10 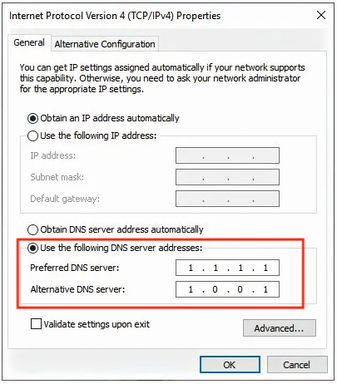 Best practice: we highly recommended to manually add these DNS addresses for best browsing experience. Here is the detail to further tweak your Network Card setting. Refer to this guide: https://www.digit.in/features/tech/tweak-network-adapter-properties-networking-ethernet-wifi-vpn-45243.html Try to disable and then re-enable your network card again after you have added the DNS setting mentioned above. Step 2 : Check Internet Browser For other Smartsheet tips, you can refer here: https://help.smartsheet.com/topics/tips-and-troubleshooting
by Staff Writer Digital transformation is touted as a leading force driving IT and business decisions. Despite the hype, it’s not delivering on the promise. In spite of surging investments, fewer than one-third of digital transformations succeed at improving a company’s performance, according to McKinsey & Company.
Yet the effective employment of digital strategies drives key benefits and across business lines, from improved productivity that fuels innovation to better business insights – but only if you approach digital transformation the right way. It’s not the underlying technology that accounts for the poor performance of so many digital transformation projects. Rather, a lack of organizational readiness is a frequent culprit, including underestimating or not understanding the work and resources required, and factors such as poor data governance and executive cohesion. Here are three key ways to beat the odds and achieve digital transformation success. by Stephen Danos Across all industries, IT departments provide the essential infrastructure for companies to operate more efficiently and effectively. They often coordinate and implement technology on a tremendous scale and ensure business continuity, from installing hardware upgrades to setting up single sign-on to improve data security. IDC recently reported that when considering a work execution platform, IT departments add adoption criteria that move beyond cost, customer validation, and implementation time. Among these necessary checks are enterprise-grade security, scalability, long-term use, APIs and integrations, and the platform’s access to a partner ecosystem. When stakeholders want to secure buy-in for new SaaS platforms, IT leaders want to outline value added, quantifiable benefits, and understand why stakeholders need the platform in the first place. However, IT teams that use Smartsheet can access several add-ons, templates, and integrations and Connectors that help improve planning, increase throughput, and streamline operations.
IT leaders can see immediate value for numerous team functions such as organizing your IT help desk, implementing software migration plans, tracking unresolved tickets, and developing new software. Smartsheet provides multiple approaches for streamlining existing IT workflows and managing projects with real-time, executive visibility. Here are seven Smartsheet solutions IT teams can use today: by Katie Bouwkamp Welcome to our employee spotlight series, featuring profiles on team members across our Bellevue, Boston, and UK offices. Learn more about the people behind the product and why Smartsheet is recognized as a great place to work! Kara Lumley is a senior product manager working within Smartsheet’s Product Engineering department. Located at the Bellevue, WA office, she’s worked at Smartsheet for just over six and a half years. Kara was one of Smartsheet’s first 40 employees, starting out on the Support team, then transitioned to be a Customer Success Manager (CSM), and eventually moved to Product Management.
by Staff Writer Change is hard – which is why managing shifts within the enterprise has evolved into a discipline in its own right. Change management refers to strategies and processes to support individuals as they navigate and adopt organizational changes, whether that’s expanding into new product lines or adopting a new technological platform.
While experts have been studying the best methods of effectively driving change since at least the 1940s, a recent study suggests that the most effective way to speed adoption in the face of organizational change is to focus not on the change itself, but to emphasize what will remain the same. by Stephen Danos The need for businesses to adopt technology and software platforms has evolved at an accelerated pace. For companies and IT teams striving to become more agile, the technology they adopt needs to enable faster decision making while ensuring the administrative controls and data security vital to scaling software platforms across their entire organization.
In a recent report, McKinsey found that agile organizations have a “70 percent chance of being in the top quartile of organizational health,” which is attributed to their ability to achieve customer centricity, quicker time to market for developing products, increased revenue growth, reduced costs, and better employee engagement. The report also identified characteristics that successful agile organizations have in common, including a willingness to embrace next-generation enabling technology. by Robin Sherwood I spend a lot of time talking with customers, particularly those who leverage Smartsheet for portfolio reporting. During the Smartsheet ENGAGE’18 customer conference, I spoke about portfolio reporting and how it can make an impact across businesses of all sizes.
I’ve worked with so many project managers (PMs) and program managers (PGMs) throughout my career, and I’ve seen a lot of traditional portfolio management tools. I believe that the generation of top-down portfolio management tools needs to be replaced by software as a service (SaaS) tools that integrate with the work being done, not just the portfolio being managed. Older tools, while effective on an individual portfolio level, force users to do extra work to manage multiple projects. This means information workers have to go out of their way to access and compile PMO status reports and tracking. |
|
Care line: +603-9212 0157
|
Leave us your inquiry |
|
This company is registered with the Ministry of Finance, Malaysia.
Equip your organisation with digital solutions & training that inspire innovation and joy at work. Copyright © 2024 57Network Consultancy Sdn. Bhd. Company Registration number : 202001020346 (1376666-K) All rights reserved. |